这道题做的时候真是一步一个坎,不说了,都是泪TAT
0x00 先访问题目链接
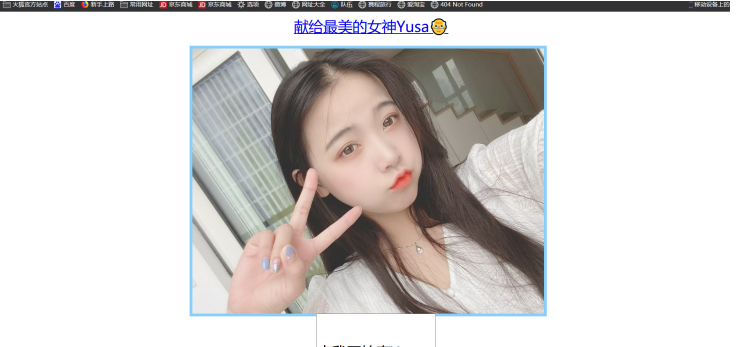
访问链接得到一张图片,格式为.webp
0x01 查看网页源代码
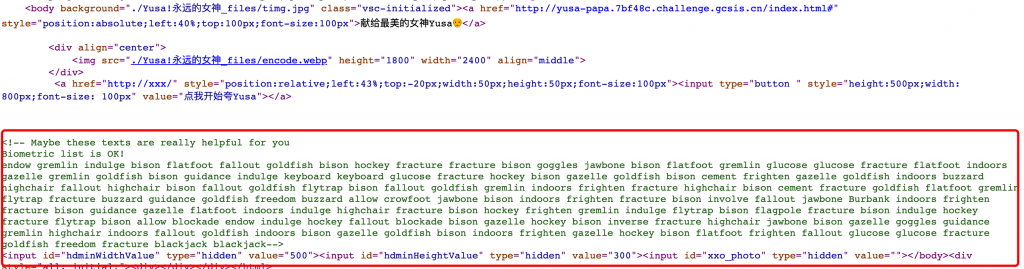
可以看到一串注释
<!-- Maybe these texts are really helpful for you Biometric list is OK! endow gremlin indulge bison flatfoot fallout goldfish bison hockey fracture fracture bison goggles jawbone bison flatfoot gremlin glucose glucose fracture flatfoot indoors gazelle gremlin goldfish bison guidance indulge keyboard keyboard glucose fracture hockey bison gazelle goldfish bison cement frighten gazelle goldfish indoors buzzard highchair fallout highchair bison fallout goldfish flytrap bison fallout goldfish gremlin indoors frighten fracture highchair bison cement fracture goldfish flatfoot gremlin flytrap fracture buzzard guidance goldfish freedom buzzard allow crowfoot jawbone bison indoors frighten fracture bison involve fallout jawbone Burbank indoors frighten fracture bison guidance gazelle flatfoot indoors indulge highchair fracture bison hockey frighten gremlin indulge flytrap bison flagpole fracture bison indulge hockey fracture flytrap bison allow blockade endow indulge hockey fallout blockade bison gazelle hockey bison inverse fracture highchair jawbone bison gazelle goggles guidance gremlin highchair indoors fallout goldfish indoors bison gazelle goldfish bison indoors frighten gazelle hockey bison flatfoot frighten fallout glucose glucose fracture goldfish freedom fracture blackjack blackjack-->
0x02 Google搜索Biometric list
搜索到了一个网站:https://goto.pachanka.org/crypto/pgp-wordlist
利用该网站进行解密
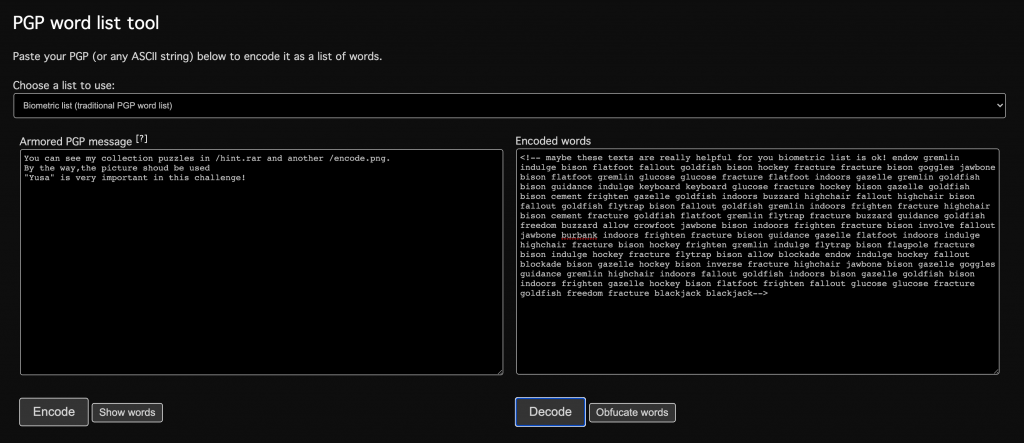
根据解出的提示,我们知道网站根目录有hint.rar和encode.png,并且Yusa很重要
0x03 分析encode.webp
hint.rar压缩包有密码,我们通过stegpy来读取隐藏在encode.webp中的密码
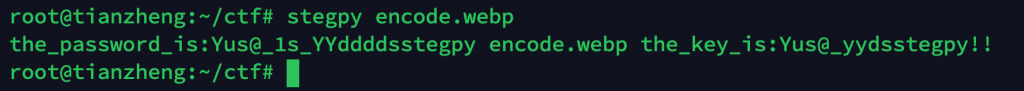
得到压缩包密码为Yus@_yydsstegpy!!
利用密码解压hint.rar,得到hint.jpg
0x04 分析hint.jpg
一个大坑,分析了好久,各种隐写工具都试过,最后用stegdetect找到隐写方式
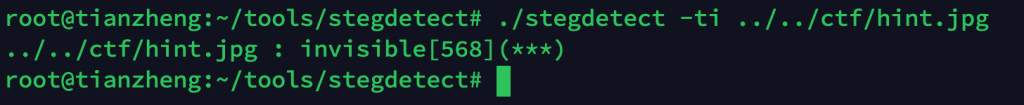
通过stegdetect得知,hint.jpg利用invisible加密
利用invisible secret对hint.jpg进行解密,密码是之前提示里的Yusa
解密后得到一个文件夹,里面有一个encode.py
import os,random
from PIL import Image,ImageDraw
p=Image.open('flag.png').convert('L')
flag = []
a,b = p.size
for x in range(a):
for y in range(b):
if p.getpixel((x,y)) == 255:
flag.append(0)
else:
flag.append(1)
key1stream = []
for _ in range(len(flag)):
key1stream.append(random.randint(0,1))
random.seed(os.urandom(8))
key2stream = []
for _ in range(len(flag)):
key2stream.append(random.randint(0,1))
enc = []
for i in range(len(flag)):
enc.append(flag[i]^key1stream[i]^key2stream[i])
hide=Image.open('source.png').convert('RGB')
R=[]
G=[]
B=[]
a,b = hide.size
for x in range(a):
for y in range(b):
R.append(bin(hide.getpixel((x,y))[0]).replace('0b','').zfill(8))
G.append(bin(hide.getpixel((x, y))[1]).replace('0b','').zfill(8))
B.append(bin(hide.getpixel((x, y))[2]).replace('0b','').zfill(8))
R1=[]
G1=[]
B1=[]
for i in range(len(key1stream)):
if key1stream[i] == 1:
R1.append(R[i][:7]+'1')
else:
R1.append(R[i][:7]+'0')
for i in range(len(key2stream)):
if key2stream[i] == 1:
G1.append(G[i][:7]+'1')
else:
G1.append(G[i][:7]+'0')
for i in range(len(enc)):
if enc[i] == 1:
B1.append(B[i][:7]+'1')
else:
B1.append(B[i][:7]+'0')
for r in range(len(R)):
R[r] = int(R1[r],2)
for g in range(len(G)):
G[g] = int(G1[g],2)
for b in range(len(B)):
B[b] = int(B1[b],2)
a,b = hide.size
en_p = Image.new('RGB',(a,b),(255,255,255))
for x in range(a):
for y in range(b):
en_p.putpixel((x,y),(R[y+x*b],G[y+x*b],B[y+x*b]))
en_p.save('encode.png')根据加密脚本写出解密脚本
0x05 EXP
from PIL import Image,ImageDraw
p = Image.open('encode.png').convert('RGB')
a,b = p.size
R=[]
G=[]
B=[]
for x in range(a):
for y in range(b):
R.append(bin(p.getpixel((x,y))[0]).replace('0b','').zfill(8))
G.append(bin(p.getpixel((x, y))[1]).replace('0b', '').zfill(8))
B.append(bin(p.getpixel((x, y))[2]).replace('0b', '').zfill(8))
R1=[]
G1=[]
B1=[]
flag=[]
for i in range(len(R)):
R1.append(int(R[i][-1:]))
G1.append(int(G[i][-1:]))
B1.append(int(B[i][-1:]))
print(R1[100:150])
print(G1[100:150])
print(B1[100:150])
for i in range(len(R1)):
flag.append(B1[i]^G1[i]^R1[i])
print(flag[100:150])
de_p = Image.new('L',(a,b),255)
c=0
for x in range(a):
for y in range(b):
if flag[c] == 1:
de_p.putpixel((x,y),0)
else:
de_p.putpixel((x, y), 255)
c=c+1
de_p.save('out.png')
利用解密脚本对encode.png进行解密,最后解出flag

大佬太强惹!!