这次比赛的杂项是真的顶,说来惭愧,比赛时就做上一个,赛后向大佬请教之后才发现,不会的地方还真的多。。。emmm
0x00 马老师的秘籍
题目下载下来是一个png图片,里面全是二维码,二维码内容大概就是马老师经典语句全文。
用binwalk查看png图片,发现里面有个压缩包
foremost分离,得到一个zip
压缩包有密码,但是可以将里面的”马老师的奇妙棋盘.jpg”解压出来
得到这么一张图片,隐约看到上面有字,我们将两张图片放到Photoshop里
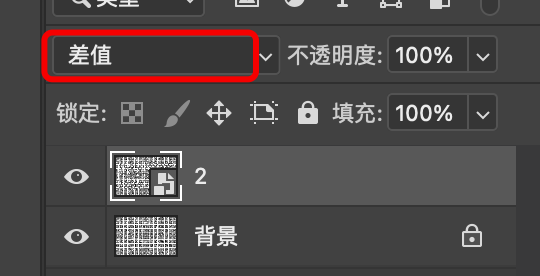
设置图层的混合模式为“差值”

就得到了这么一张图片,根据图片内容计算MD5
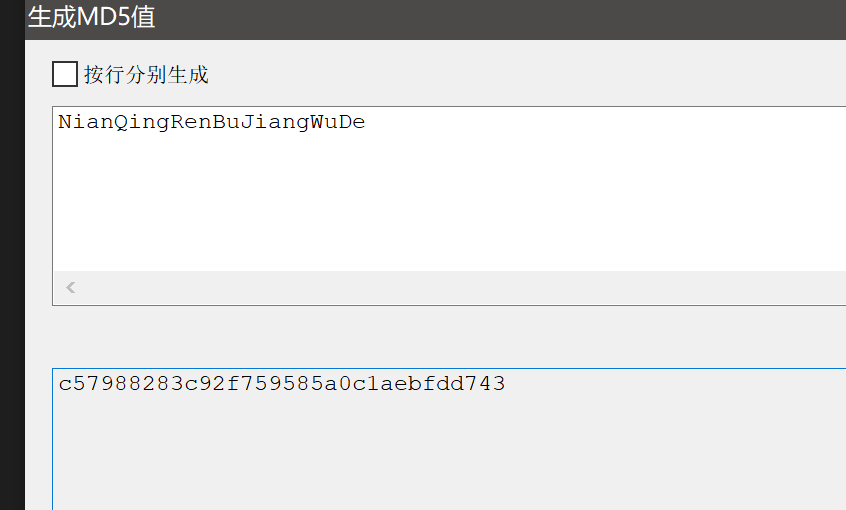
用该MD5即可解开压缩包
我们得到“闪电五连鞭.txt”和“GoodLuck.txt”,打开GoodLuck.txt
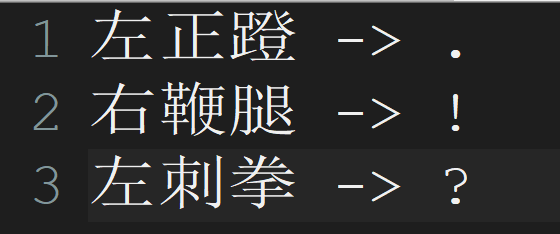
再看闪电五连鞭.txt
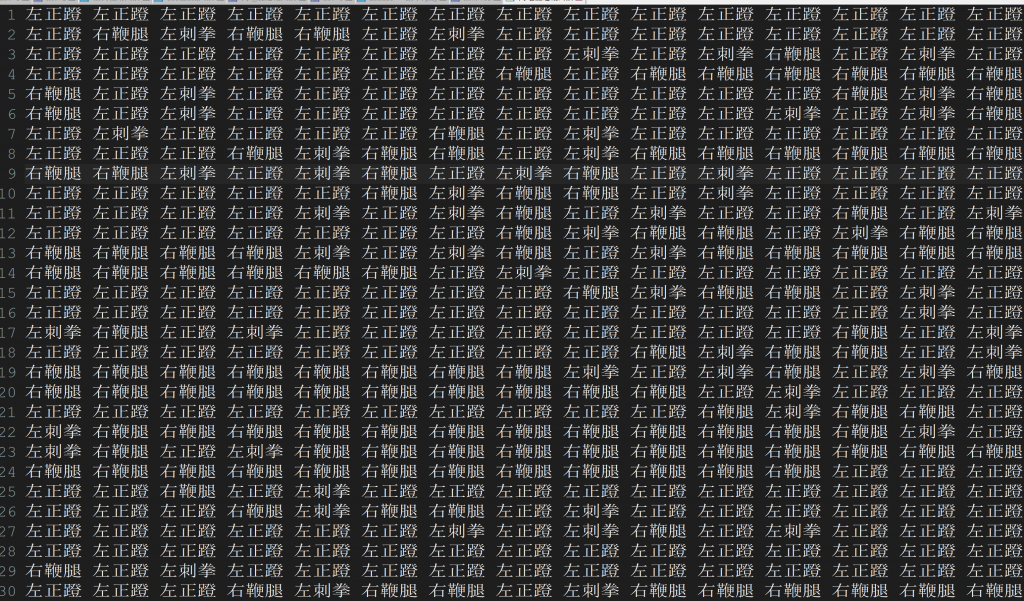
按照提示,将“左正蹬”“右鞭腿”和“左刺拳”进行替换
得到Ook!编码
. . . . . . . . . . . . . . .
. ! ? ! ! . ? . . . . . . . .
. . . . . . . . ? . ? ! . ? .
. . . . . . . ! . ! ! ! ! ! !
! . ? . . . . . . . . . ! ? !
! . ? . . . . . . . . ? . ? !
. ? . . . . ! . ? . . . . . .
. . . ! ? ! ! . ? ! ! ! ! ! !
! ! ? . ? ! . ? ! . ? . . . .
. . . . . ! ? ! ! . ? . . . .
. . . . ? . ? ! . ? . . ! . ?
. . . . . . . ! ? ! ! . ? ! !
! ! ! ! ? . ? ! . ? ! ! ! ! !
! ! ! ! ! ! . ? . . . . . . .
. . . . . . . . ! ? ! ! . ? .
. . . . . . . . . . . . . ? .
? ! . ? . . . . . . . . ! . ?
. . . . . . . . . ! ? ! ! . ?
! ! ! ! ! ! ! ! ? . ? ! . ? !
! ! ! ! ! ! ! ! ! ! . ? . . .
. . . . . . . . . . ! ? ! ! .
? ! ! ! ! ! ! ! ! ! ! ! ! ? .
? ! . ? ! ! ! ! ! ! ! ! ! ! !
! ! ! ! ! ! ! ! ! ! ! ! . . .
. . ! . ? . . . . . . . . . .
. . . ! ? ! ! . ? . . . . . .
. . . . . . ? . ? ! . ? . . .
. . . . . . . . . . . . . . .
! . ? . . . . . . . . . . . .
. . . ! ? ! ! . ? ! ! ! ! ! !
! ! ! ! ! ! ! ! ? . ? ! . ? !
! ! ! ! ! ! . . . . . . . . .
. . . . ! . ? . . . . . . . .
. . . . . ! ? ! ! . ? . . . .
. . . . . . . . ? . ? ! . ? .
. . . . . . . . . . . . . . .
. . . . ! . ? . . . . . . . .
. . . . . . . ! ? ! ! . ? ! !
! ! ! ! ! ! ! ! ! ! ! ! ? . ?
! . ? ! ! ! ! ! . ! ! ! ! ! !
! . . . . . ! . . . ! . ! ! !
. ? . . . . . . . . . . . . .
. . ! ? ! ! . ? . . . . . . .
. . . . . . . ? . ? ! . ? . .
. . ! . ? . . . . . . . . . .
. . . . . ! ? ! ! . ? ! ! ! !
! ! ! ! ! ! ! ! ! ! ? . ? ! .
? ! ! ! ! ! . . . . . . . . .
! . ? . . . . . . . . . . . .
. ! ? ! ! . ? . . . . . . . .
. . . . ? . ? ! . ? . . . . .
. . . . . . . . . ! . ? . . .
. . . . . . . . . . ! ? ! ! .
? ! ! ! ! ! ! ! ! ! ! ! ! ? .
? ! . ? ! ! ! ! ! ! ! ! ! ! !
! ! ! ! ! ! ! ! ! ! ! ! . ? .
. . . . . . . . . . . . . . !
? ! ! . ? . . . . . . . . . .
. . . . ? . ? ! . ? . . . . .
. ! . ? . . . . . . . . . . .
. . . . ! ? ! ! . ? ! ! ! ! !
! ! ! ! ! ! ! ! ! ? . ? ! . ?
! . ! ! ! ! ! ! ! ! ! . ? . .
. . . . . . . . . . . . . ! ?
! ! . ? . . . . . . . . . . .
. . . ? . ? ! . ? ! . ? . . .
. . . . . . . . . . ! ? ! ! .
? ! ! ! ! ! ! ! ! ! ! ! ! ? .
? ! . ? ! ! ! ! ! ! ! ! ! ! !
! ! ! ! ! ! . ? . . . . . . .
. . . . . . ! ? ! ! . ? . . .
. . . . . . . . . ? . ? ! . ?
. . . . . . . . . . . . . . .
. ! . ? . . . . . . . . . . .
. . ! ? ! ! . ? ! ! ! ! ! ! !
! ! ! ! ! ? . ? ! . ? ! ! ! !
! ! ! ! ! ! ! ! ! ! ! . ! ! !
! ! . ! ! ! ! ! . . . . . ! .
! . ? . . . . . . . . . . . .
. ! ? ! ! . ? . . . . . . . .
. . . . ? . ? ! . ? . . . . .
. . . . . . . . . . . ! . . .
. . . . . . . . ! . ! ! ! ! !
! ! ! ! ! ! . ? . . . . . . .
. . . . . . ! ? ! ! . ? ! ! !
! ! ! ! ! ! ! ! ! ? . ? ! . ?
! ! ! ! ! ! ! ! ! . ? . . . .
. . . . . . . . . . . . . ! ?
! ! . ? . . . . . . . . . . .
. . . . . ? . ? ! . ? . . . .
. . . . ! . ? . 在线解密即可得到flag

0x01 FakePic
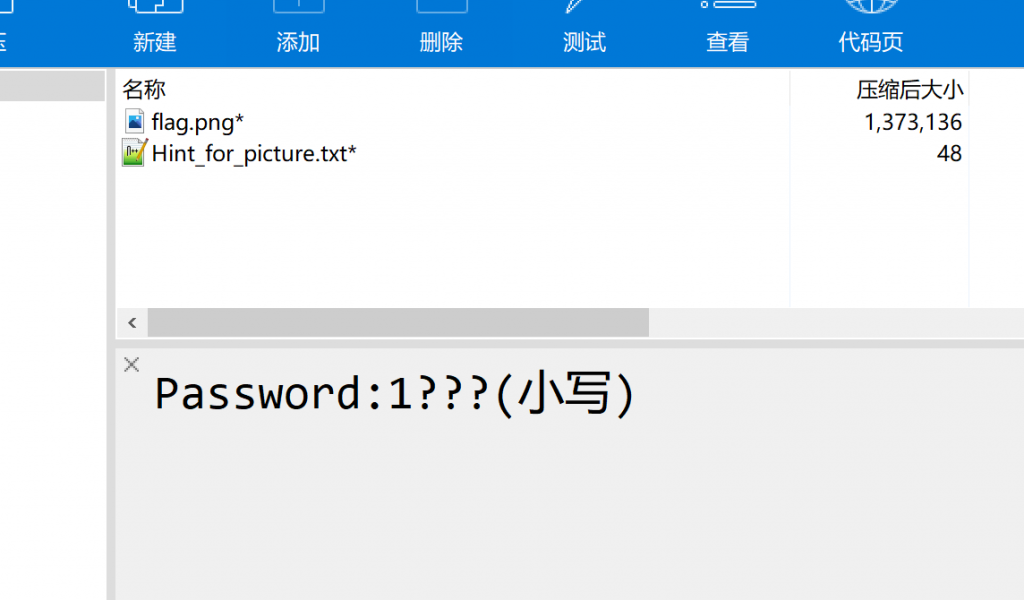
题目下载下来是个压缩包,有密码,并提示:Password:1???(小写)
利用Archive工具进行爆破,提示不支持。
那么这个rar应该是rar5加密,我们利用hashcat进行爆破。
打开kali
root@kali# rar2john 1.rar
root@kali# hashcat -a 3 -m 13000 --force "\$rar5\$16\$6922f72762b2fb0ce74d7d7d3596e501\$15\$3155b2f407666e39715e2b878873ac6b\$8\$ac212f343c4b0cda" "1?l?l?l" --show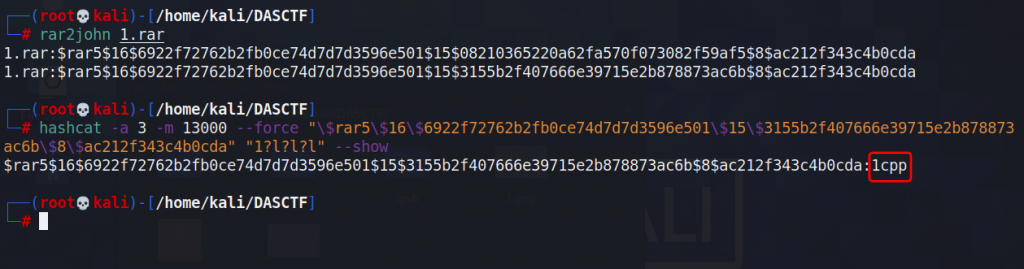
解得密码为1cpp
解压文件得到flag.png和hint
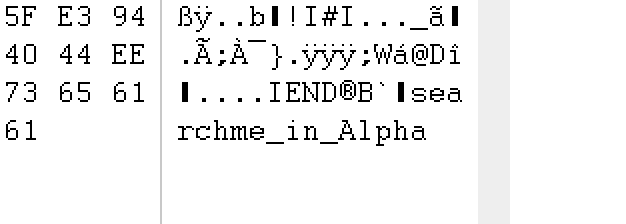
hint没太看懂,用winhex查看png图片末尾
我们写个脚本将前几位Alpha通道的值打印出来
from PIL import Image
r = Image.open('flag.png')
width,height = r.size
# print(width)
# print(height)
for y in range(100):
x = 0
alpha = r.getpixel((x,y))[-1]
print(alpha)
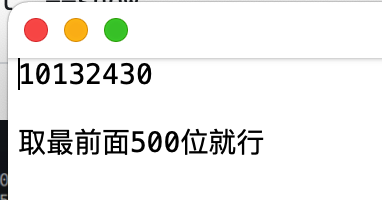
打印完得到的数字,发现这几个数都是2的倍数,且倍数都不大。结合前面的提示(而且提示的长度还为8)。那么就猜测提示的作用是这样的:10132430这8个为一轮一直循环。如果刚好算出来的pow(2,x)和Alpha通道的值一样,那么就为1,否则就为0。
解题脚本如下:
from PIL import Image
r = Image.open('flag.png')
width,height = r.size
# print(width)
# print(height)
flag = ''
hint = [1,0,1,3,2,4,3,0]
n = -1
for y in range(500):
x = 0
alpha = r.getpixel((x,y))[-1]
n += 1
if pow(2,hint[n % 8]) == alpha:
flag += '1'
else:
flag += '0'
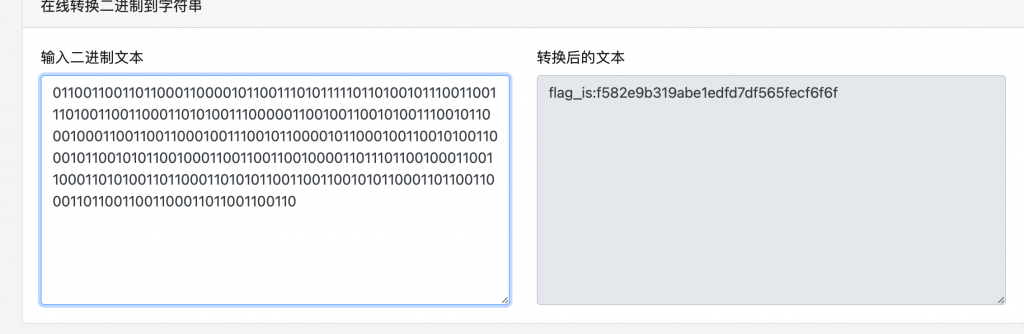
print(flag)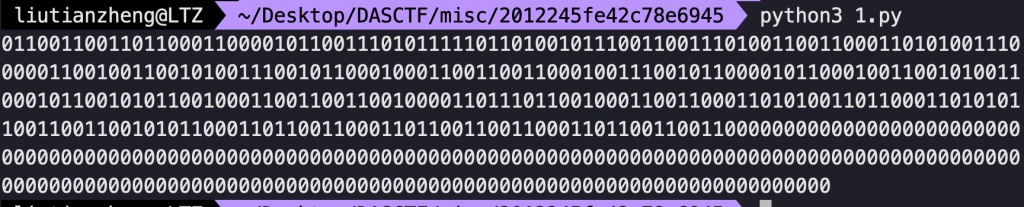
后面的000自己删一下
二进制转字符串即可得到flag
0x02 FakePixel
题目下载下来后,是一个BMP图片和一个加密脚本
根据加密脚本很容易推出解密脚本
from PIL import Image
import math
def decode(le,hi):
x,y = 0,0
sec = ''
for y in range(hi):
for x in range(le):
r,g,b = im.getpixel((x,y))
sec += chr(int(b))
print(chr(int(b)))
return sec
if __name__ == '__main__':
Image.MAX_IMAGE_PIXELS = None
im = Image.open("./FakePicture.bmp")
print(im.mode)
kuan = 16659
chang = 16658
flag = decode(kuan,chang)
filename = 'test.txt'
with open(filename, 'w') as file_object:
file_object.write(flag)解密后我们得到一个txt文件,我们查看txt结尾位置,04034B50,很明显的逆序,我们用脚本逆回去
f = open("text.txt",'rb').read()
d = open("1.zip",'wb')
d.write(f[::-1])我们得到了一个压缩包
压缩包备注里有一串Ook!编码,解密后得到压缩包密码:dasctf_1s_s0_funny
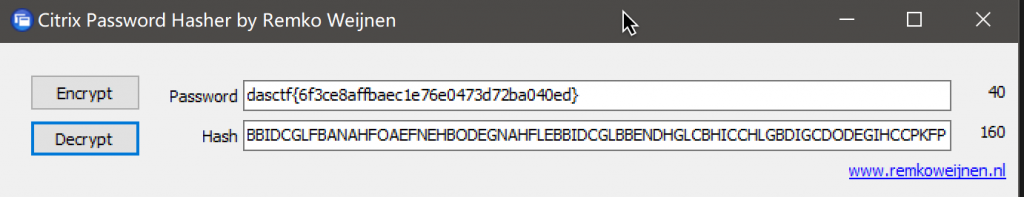
打开视频文件,在视频中看到一个MaxiCode

上网解密,得到Citrix CTX1

Citrix CTX1是一种加密算法,但是没有密文,继续分析视频
在视频结尾看到藏了一个mp3文件,用winhex提取出来
用MP3Stego需要密码,用Audacity也没有分析出任何东西
向大师傅请教之后得知,mp3音频帧存在帧头信息
用010Editor打开
我们看到文件有个private_bit位
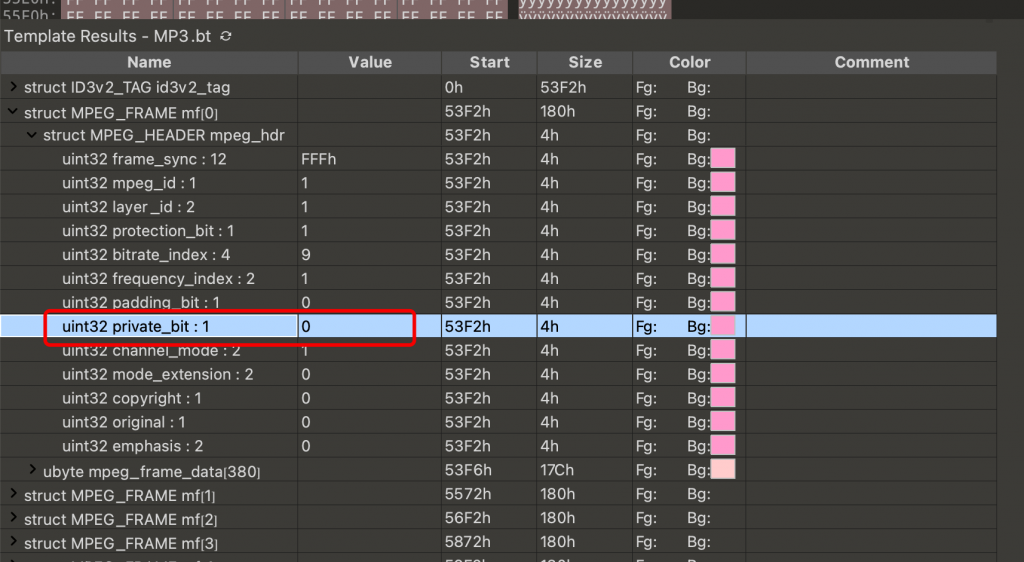
写脚本将所有的private_bit位提取出来
import re
import binascii
n = 21492
result = ''
fina = ''
file = open('3.mp3','rb')
while n < 2543601 :
file.seek(n,0)
n += 384
file_read_result = file.read(1)
read_content = bin(ord(file_read_result))[-1]
result = result + read_content
print result[::-1] #由于打印出来解码为乱码,这里倒序输出输出
0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000011001000110011001101000011000000110111010001010011010101000101001101110100000100110100001100010011010000110001001101000011000100110100001100010011010000110001001100110100010000110011010001000011010101000011001101100100001000110110010001100011001000110100001101000100001000110011001101100011001001000011001101000100000100110100001110000011011101000101001101000100010000110100001100010011010000110110001101100011001000110111010000010011011100110011001101000011100000110110001101100011010101000110001101000100010000110100010000010011001000111001001101110100010100110111001100110011010000111000001101000011000100110010001100010011010000110001001101100100010100110101010000010011011000110010001101010100011000110100001110000011010000110010001101000011001100110111001101000011011100110010001101100011100000110011001100100011010000110110001101110011000100110100001100100011001001000110001101110011010000110101001100110011010000110110001101000011000100110110001110000011010000111000001100110011100100110101010001100011010000111000001101000100000100110101010000110011011101000101001100110011100100110111001100010011001100110011001100100100011000110111010001010011011100110010001101100100011000110011001100100011011101000001001100100011100000110100001101110011010101000001001100100011000100110111010001000011011100110011001101000011000100110110001100100011011100110001001101010100011000110101010000010011001101000010001100110011011000110100010001000011010000110001001101100011011000110010001110000011011000110110001100110100001000110100010001000011001100110110001100100011100100110100001100010011011100110011001100110011000100110111010001010011011100110101001100110011001000110110001101000011001100110010001101000011000100110111010001010011001000111000001100110011100100110101010000010011010100110110001101010011001100110111001101110011010000110001001100100011100100110011001100010011001000111001001101110011010100110111001101110011011100110010001100100011100100110011001100100011011100110111001101000011100000110011001100100011010101000110001101000011000100110011001101100011001100111001001101000011000100110100010001000011001100110001001100100011100100110111001101010011011100110111001101010011001100110011001100110011010000110001001101110100010100110010001110000011010000110111001101010100000100110010001100010011011000110100001101000011000100110111010001010011001100110010001100110011000100110100001101110011010000110011001101010011011000110100010000010011010101000001001101110100010100110100001100110011001000111000001101010100000100110011010000100011010000110011001101000100000100110010001100010011011101000101001101100011011000110111001100010011010100110110001100100100011000110110001101100011011101000100001101100011011000110011001100100011010100110110001100100011100000110111001101010011010101000001001100110100001000110110010001010011011001000101001101110011001100110100010000100011010001000001001101010011001100110111010001010011001001000010001101100011001100110101001100010011011000110011001101010100000100110011001100010011011100110110001101000011001000110101001100000011010000110101001100110011100100110111010000010011001101000110001101010100000100110101001100000011011001000110001101110011001000110100001100000011001000110011001101000011000000110010001101100011011101000110001101010011010100110101010001010011010001000100001101100100001000110011001100100011010000110100001101010011001000110011001101010011010000110101001101100100001000110100001101000011001100110000001101010011010000110110001100110011010000110001001101000011000100110100001100010011001101000100001100110100010000110101010001010011001000110011001101110100010100110100001100000011000000110000将前面的0删掉,然后转十六进制再转ascii
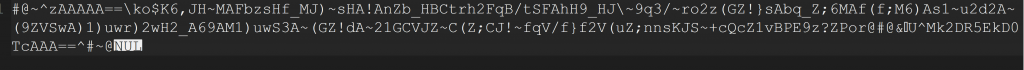
保存成.vbe格式的文件,然后解密:https://master.ayra.ch/vbs/vbs.aspx
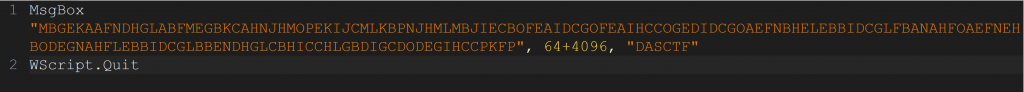
解密完得到一个hash值,google搜索Citrix CTX1,能搜到一个工具,用工具来解密,即可得到flag